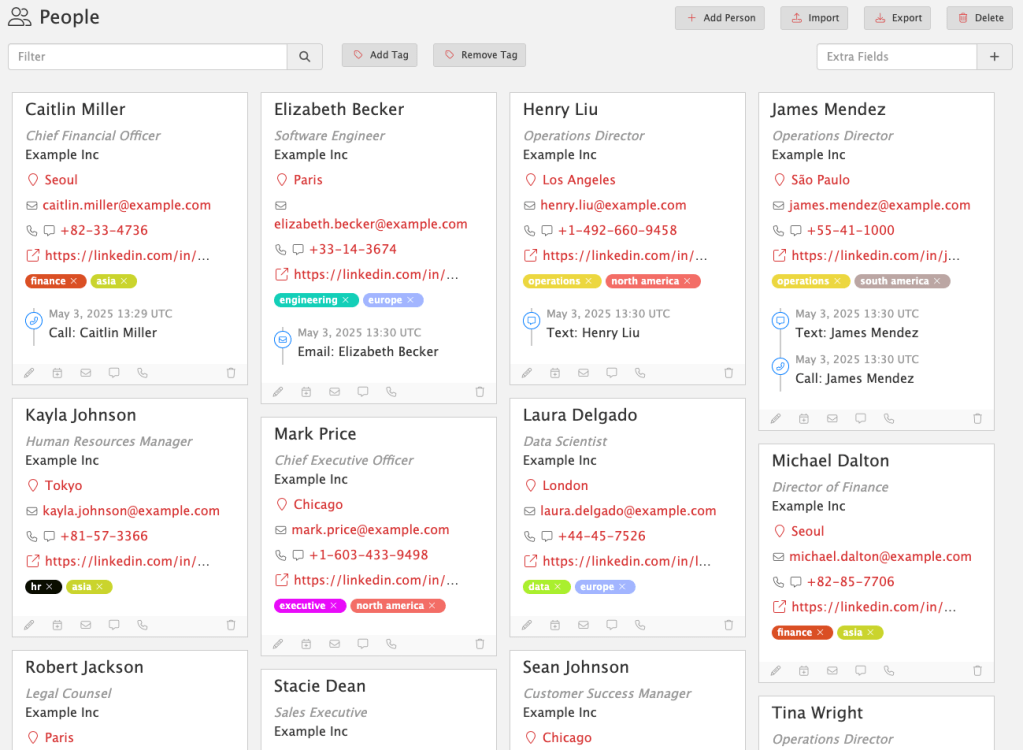
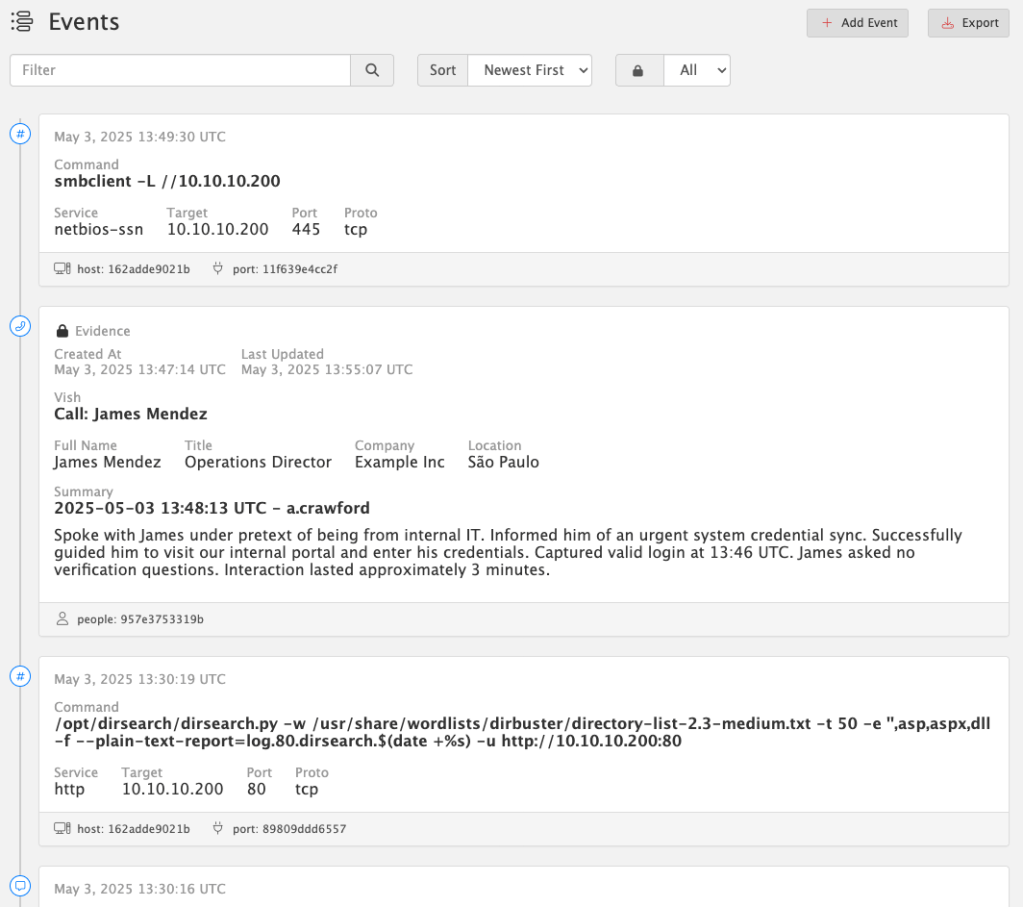
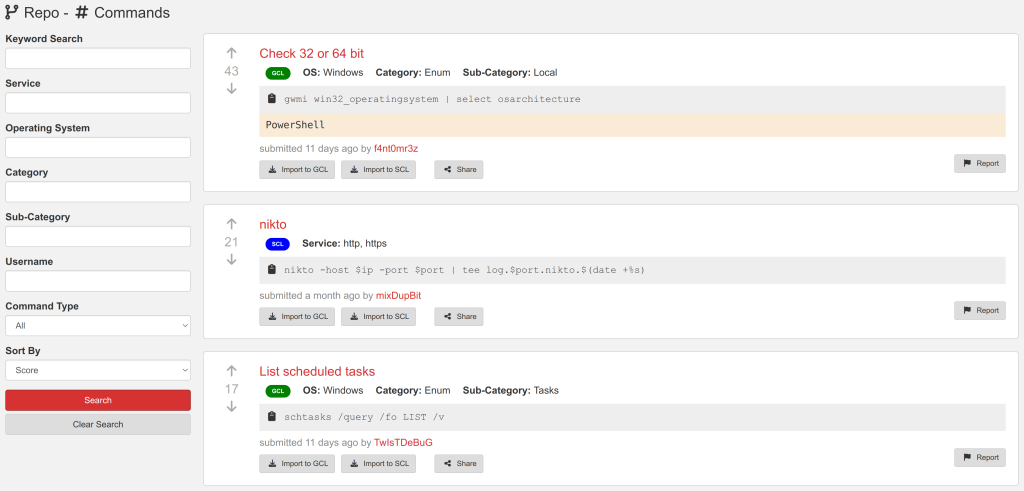
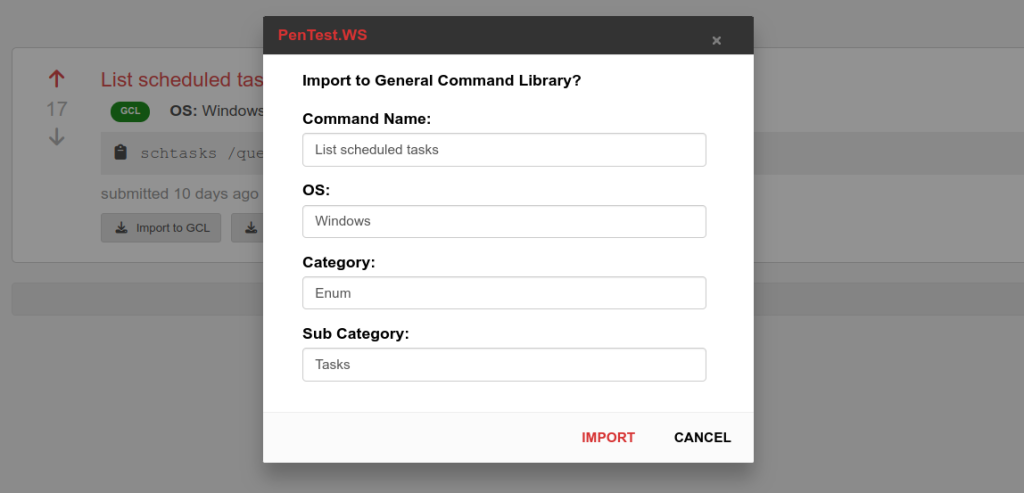
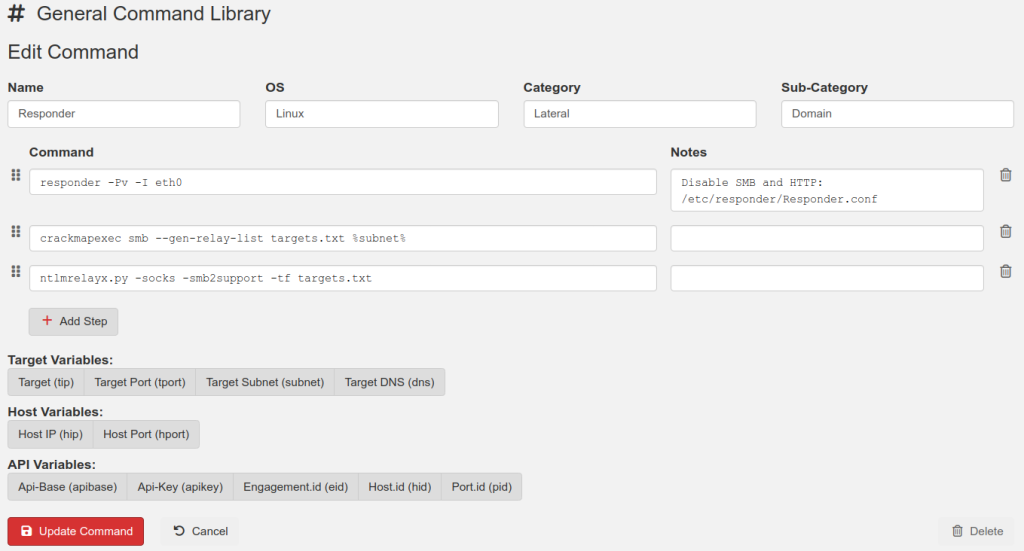
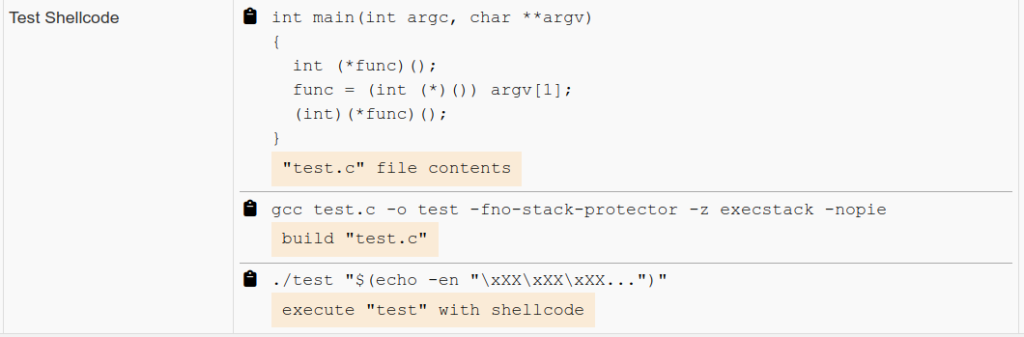
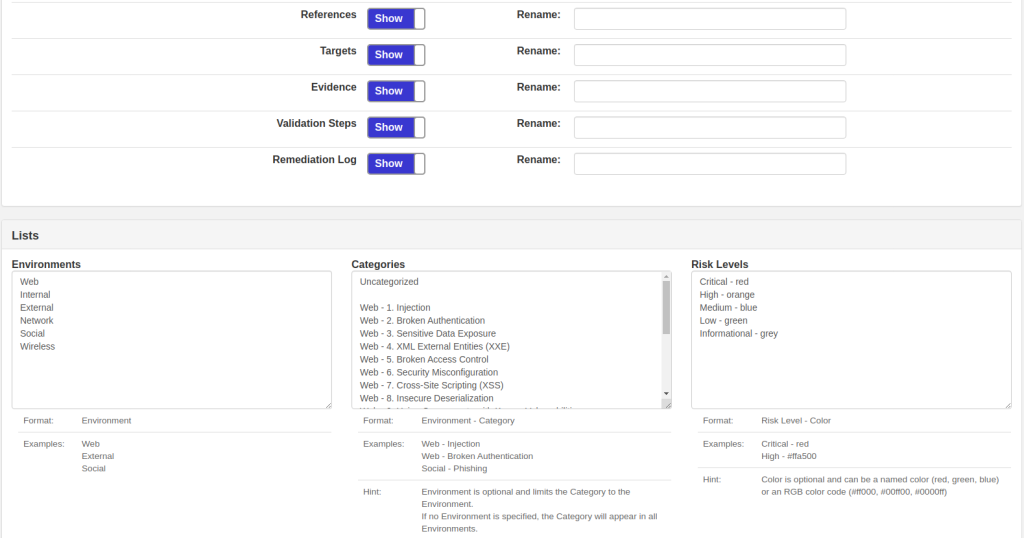
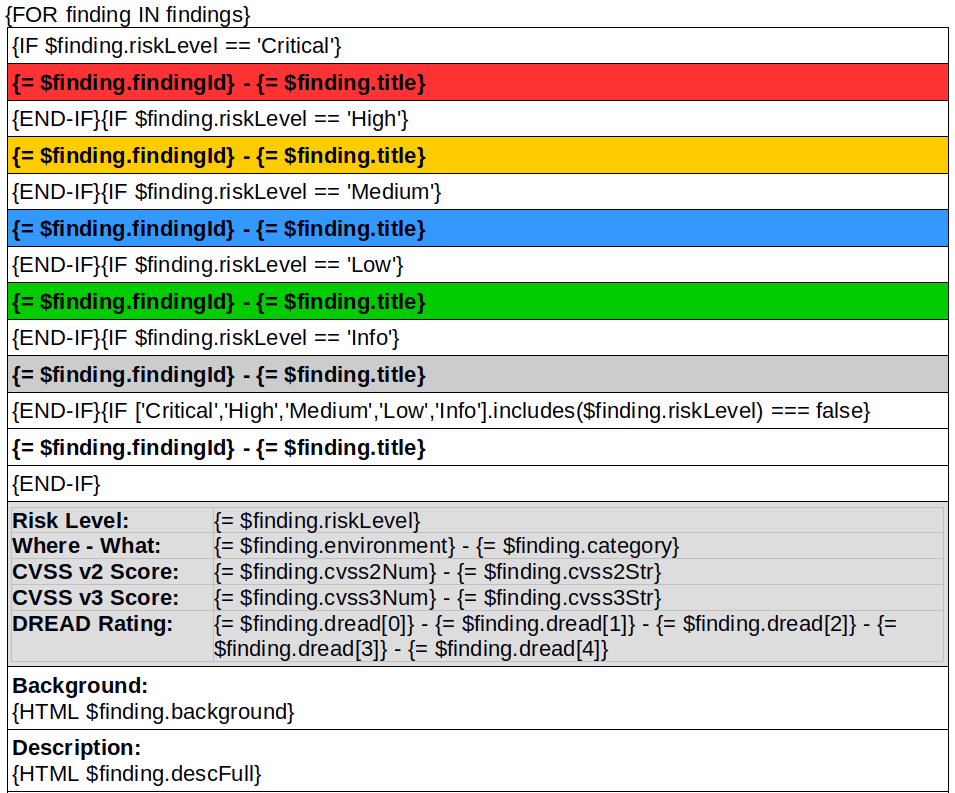
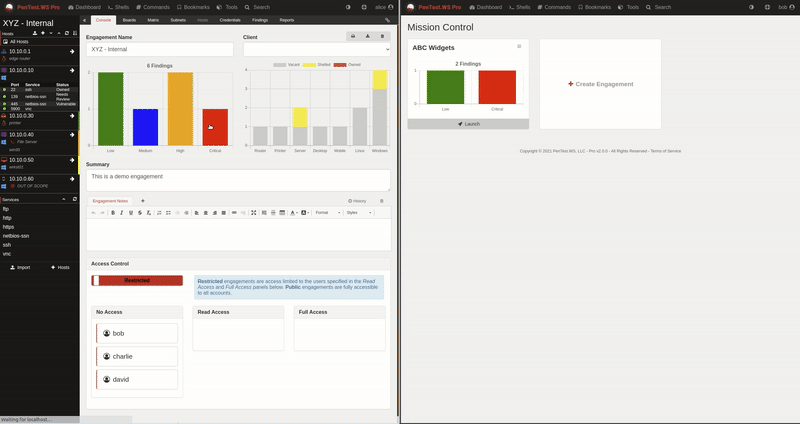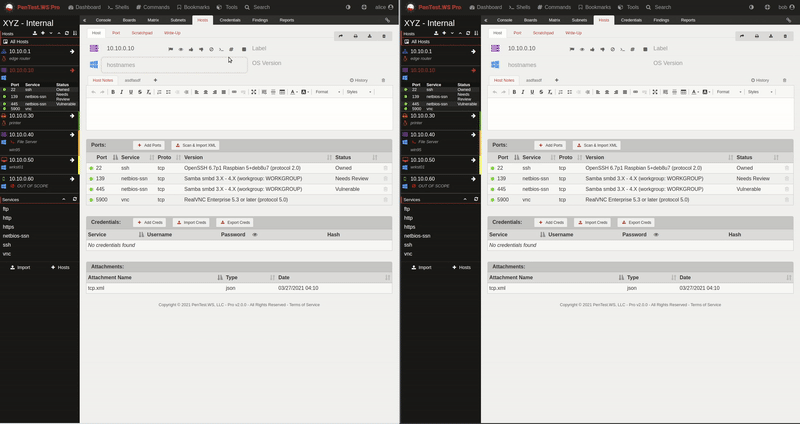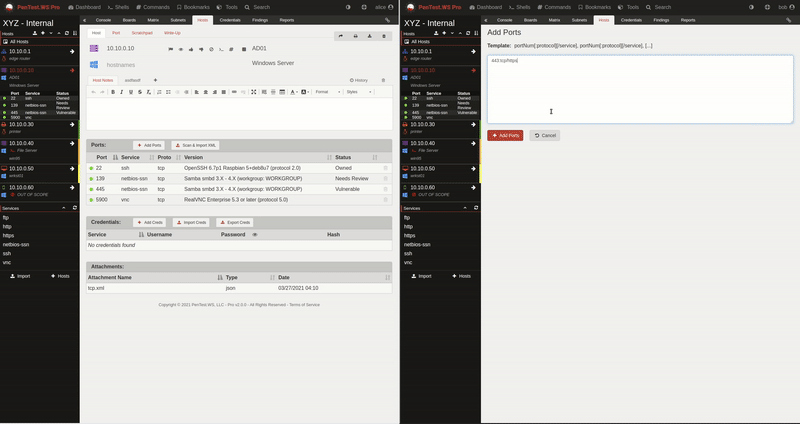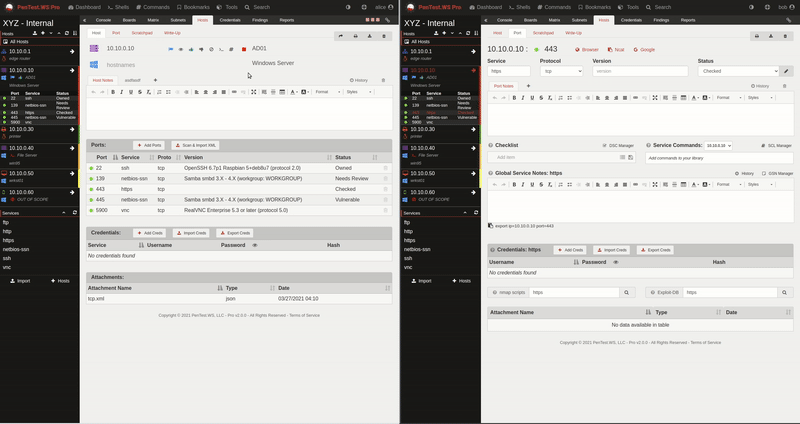
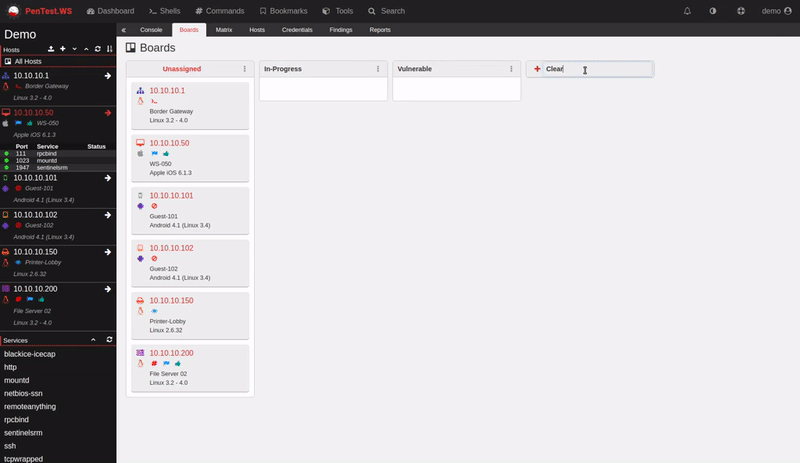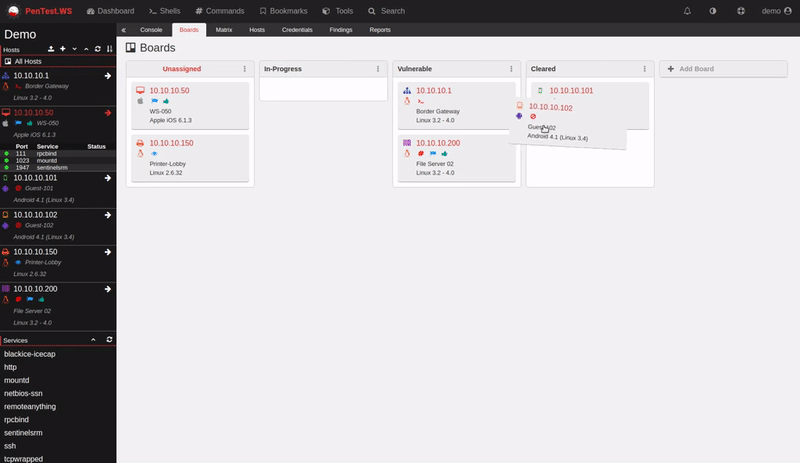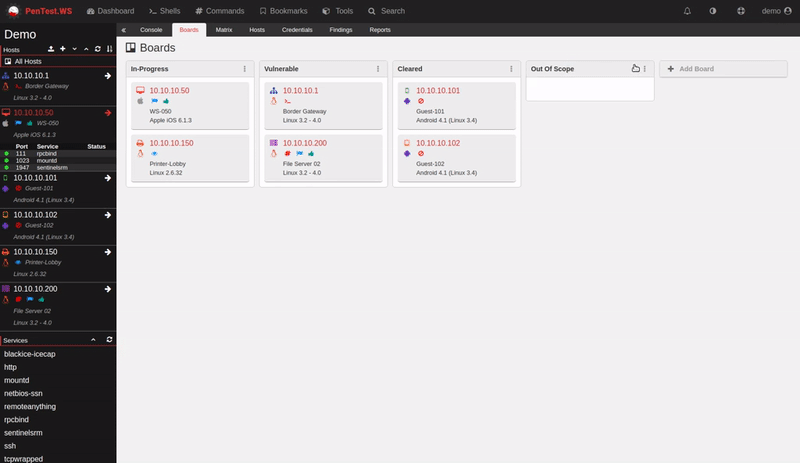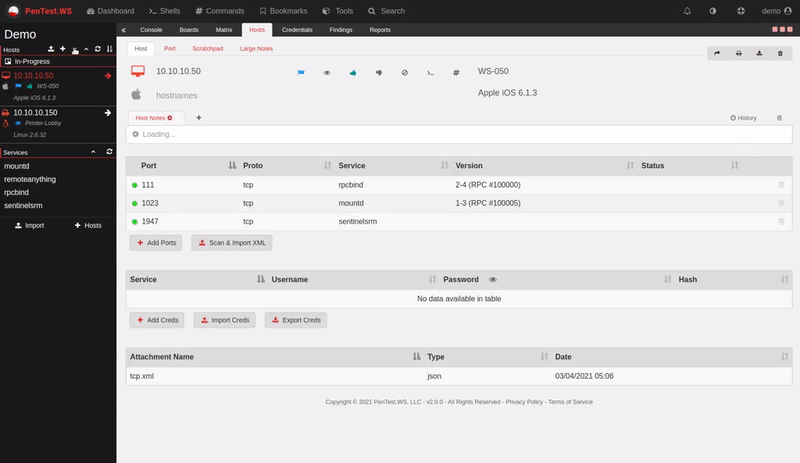
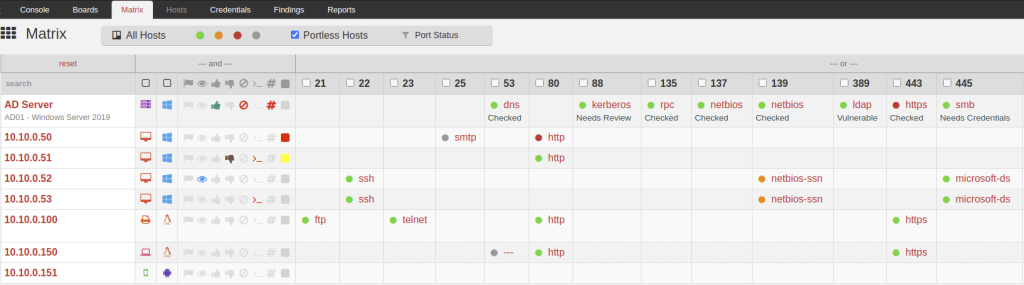
For almost a decade, we’ve had the privilege of watching many of you grow. What began as individual practitioners and small teams has evolved into established security organizations operating across regions and time zones. PenTest.WS has supported that growth through thousands of engagements, countless findings, and more report iterations than we can reasonably count.
Today, we’re announcing something we’ve been building quietly for the past two years: Neuron – a security engagement management platform designed for teams operating at enterprise scale.
Before we go any further: PenTest.WS isn’t going anywhere.
Your Hobby and Pro accounts will continue working exactly as they do today. This isn’t a sunset announcement. It’s an expansion.
The Problem With Scale
As your teams have grown, we’ve heard the same challenges come up again and again.
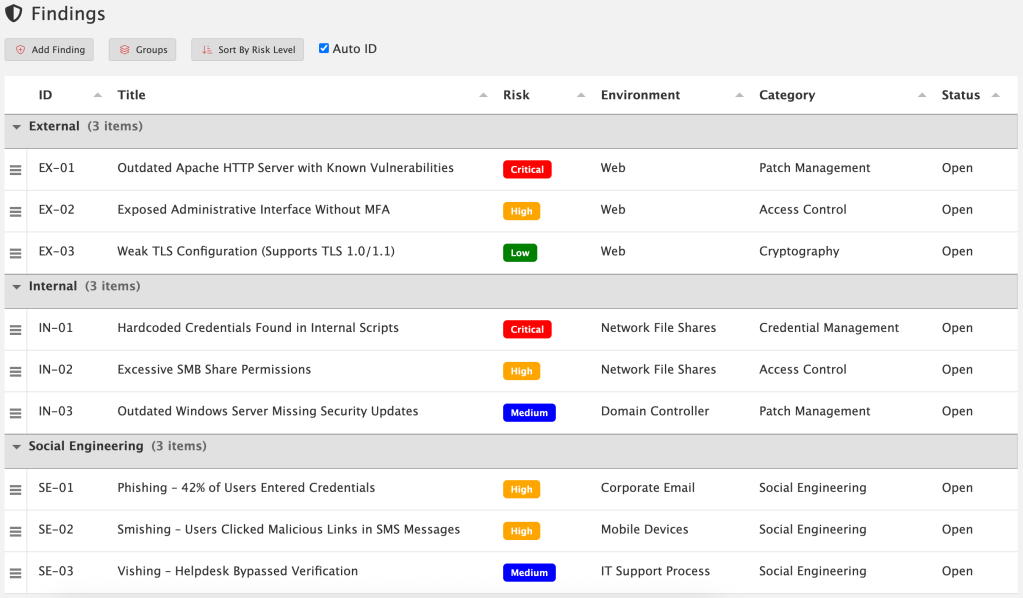
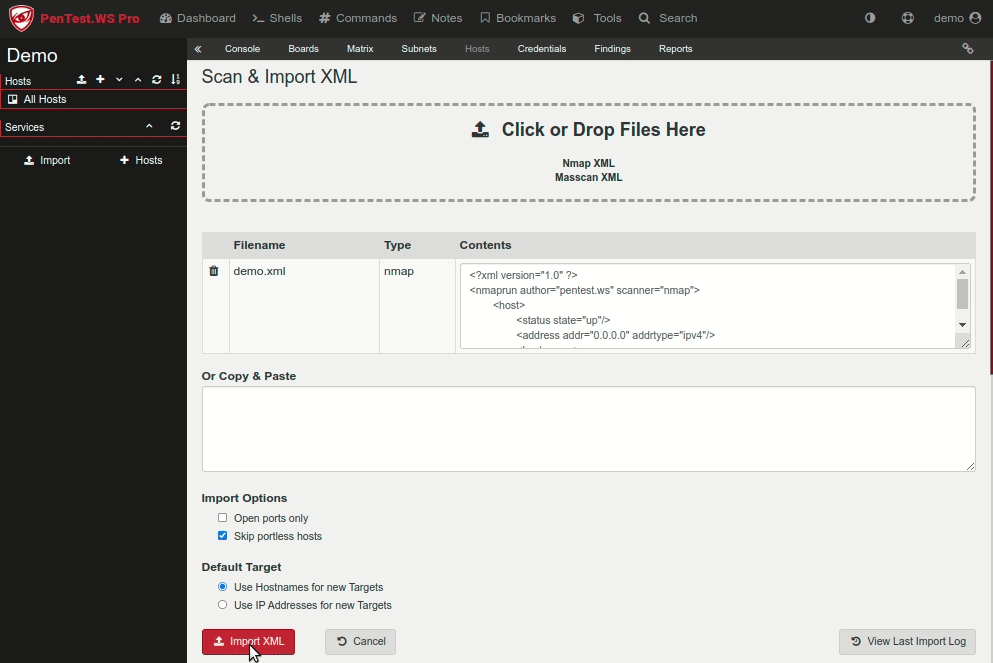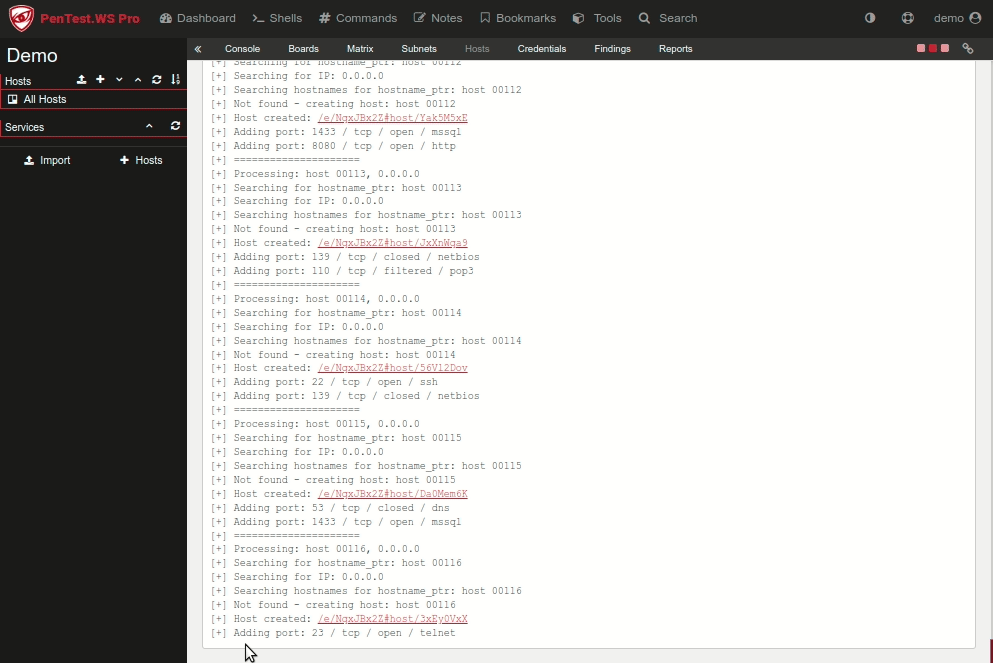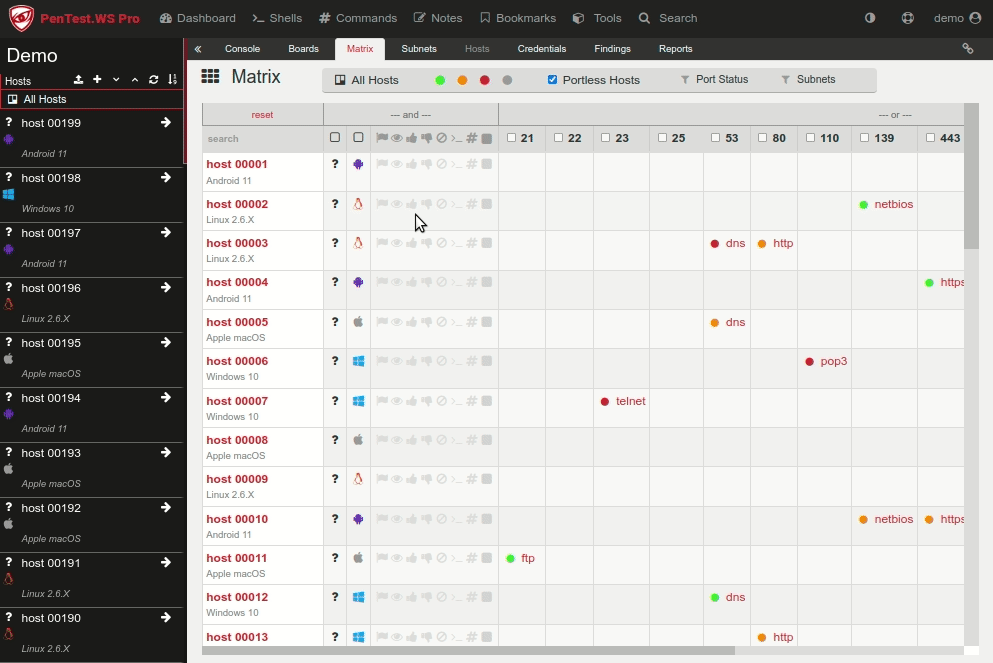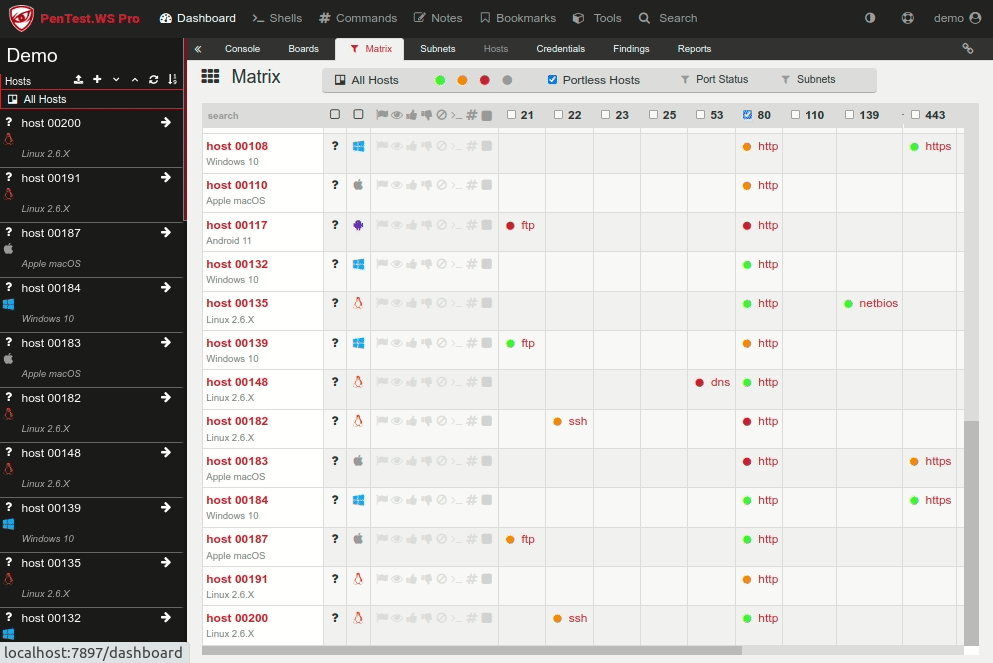
Your report turnaround is bottlenecked by documentation, not testing. Your QA process is held together with spreadsheets, email threads, and Slack messages that start with “hey, can you review this?”
Your clients want visibility into engagement progress without you manually exporting PDFs every few days.
PenTest.WS Pro gave you the foundation: self-hosted deployments, real-time collaboration, and air-gapped support. But enterprise teams managing dozens of concurrent engagements need more than a foundation. They need workflows built for scale.
So that’s exactly what we built.
Meet Neuron

Neuron takes everything you know from PenTest.WS and adds the enterprise capabilities that larger teams have been asking for. Built by the same team, with nearly a decade of experience watching how security teams actually work.
Here’s what’s new:
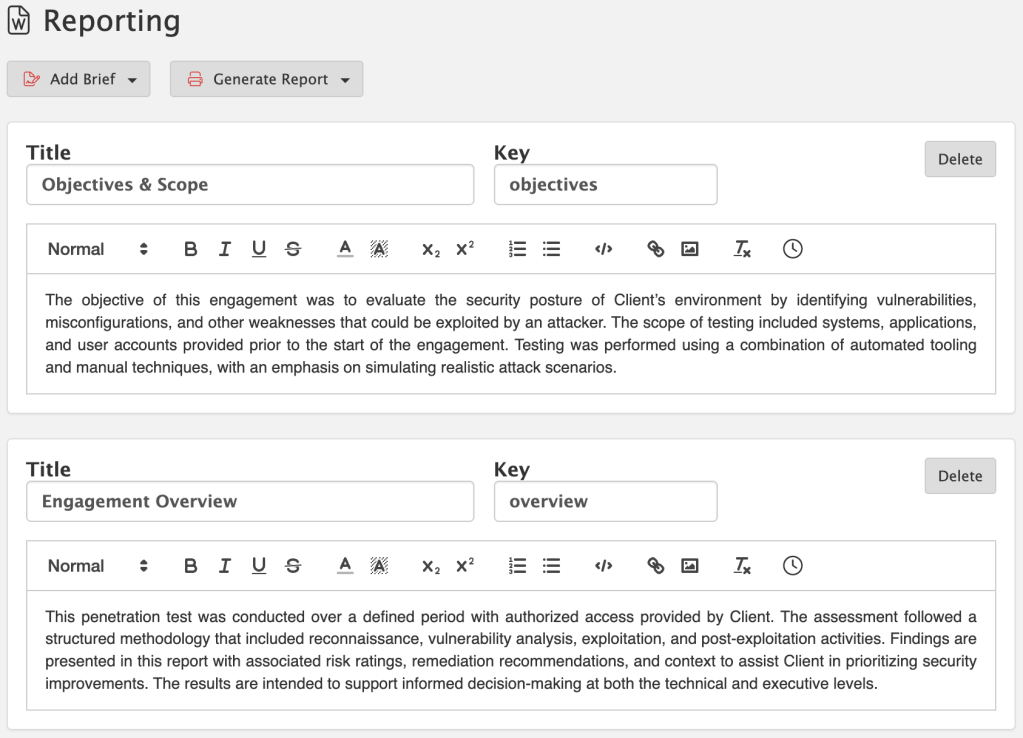
AI-Powered Reporting
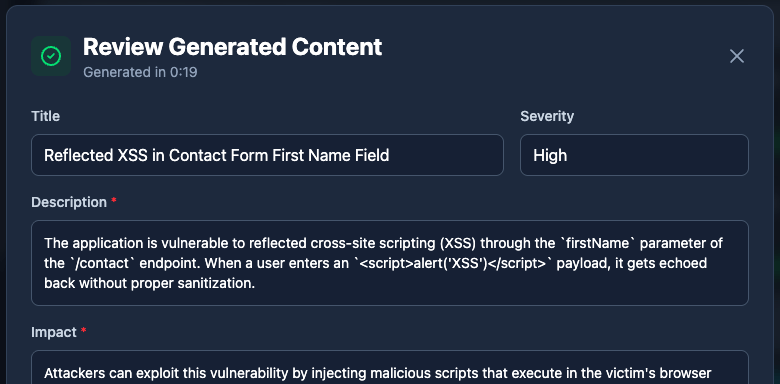
Your team’s expertise should go into finding vulnerabilities, not writing the same boilerplate for the hundredth time.
Neuron’s AI reporting assistant generates consistent, professional content across all your reporting fields such as finding descriptions, business impact, and remediation guidance. Combined with your reusable finding library that now supports scope-specific variants, your team can document findings in seconds instead of hours.
Teams running Neuron are delivering reports up to 3x faster than their previous workflows. That’s not marketing speak, it’s consistent feedback from early adopters.
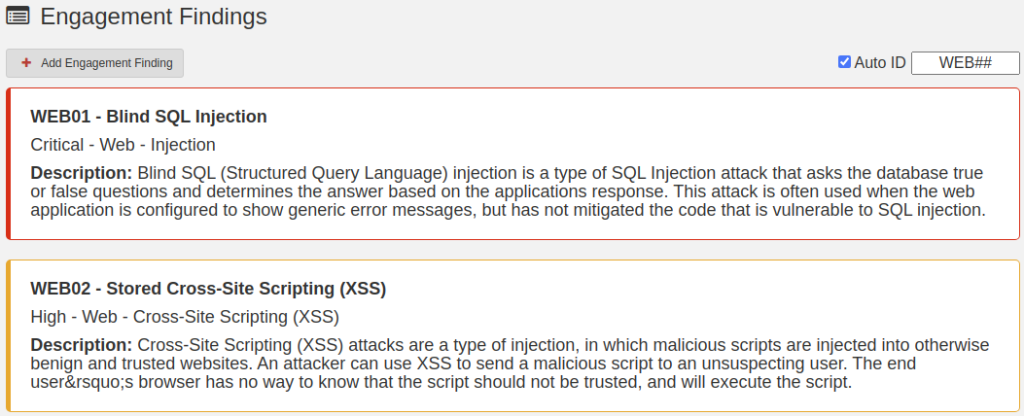
Multi-Stage QA Workflows
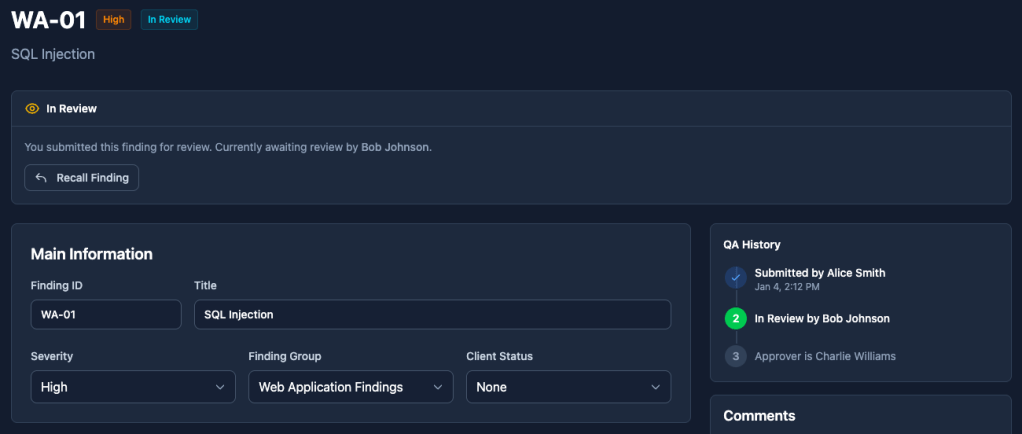
Quality assurance shouldn’t be an afterthought bolted onto your process. Neuron makes it native.
Every finding moves naturally through your QA pipeline: Draft → Review → Approved. You set who can review, and who can approve. The system enforces it automatically.
Role-based access controls ensure the right people have the right permissions. A complete audit trail tracks every change, every approval, every comment – critical for compliance-heavy clients and government work.
No more wondering if that finding was reviewed. No more “who approved this?” conversations. No more findings slipping into client reports without proper sign-off. The workflow catches it before it becomes a problem.
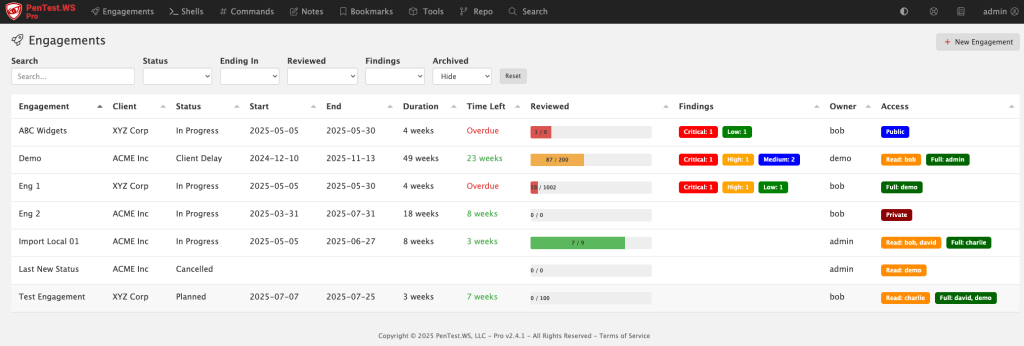
For teams juggling multiple engagements across multiple clients, this alone changes how you operate.
Client Portal
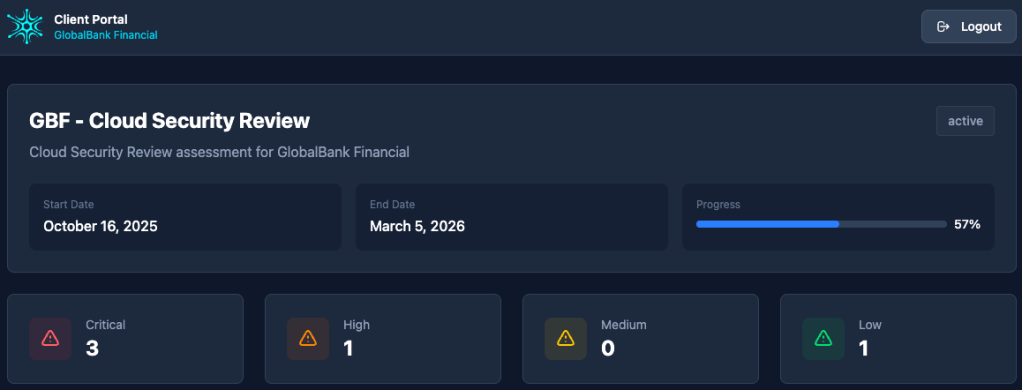
Stop exporting PDFs. Stop sending slide deck status update emails. Give your clients what they actually want: visibility.
Neuron’s client portal provides secure, read-only access for your clients to track engagement progress in real-time. They see what you want them to see, when you want them to see it. Findings appear as they’re approved through your QA workflow – not before.
Set up time-bound file sharing links for deliverables. Brand the portal with your firm’s logo and colors. Your clients get a professional experience; you get fewer “what’s the status?” emails.
For firms managing ongoing relationships with enterprise clients, the portal transforms how you communicate progress without adding overhead to your team.
Who It’s For
If you’re a solo operator or small team happy with PenTest.WS Pro, stay where you are. It still delivers everything you need for individual practitioners and small teams.
Neuron is purpose-built for teams that have outgrown individual workflows:
- Boutique pentesting firms scaling from 5 to 50 operators who need structured QA
- Enterprise internal security teams managing ongoing assessment programs with compliance requirements
- MSSPs juggling multiple client engagements who need portal access for their customers
- Government and defense contractors requiring audit trails and approval workflows
If your team is wrestling with QA bottlenecks, client communication overhead, or documentation that takes longer than the testing – Neuron was built for you.
Two Products, One Team
We want to be crystal clear: PenTest.WS and Neuron are separate products serving different needs.
PenTest.WS remains fully supported for Hobby and Pro tier users. We’re not abandoning the platform that got us here. We’re committed to keeping PenTest.WS running smoothly for the community that’s trusted us for years.
Think of it this way: PenTest.WS is the toolkit for operators. Neuron is the platform for enterprise operations. Different scales, same team behind both.
See It In Action
We’ve put everything we’ve learned from nearly a decade of building pentesting tools into Neuron. We’d love to show you what it can do.
Visit neuron.ws to explore the platform, see the full feature breakdown, and request a personalized demo.
Thanks for being part of this journey. We built PenTest.WS because we all needed better tooling. We built Neuron because we watched teams outgrow those tools into needing enterprise workflows.
Same mission. Bigger scale.
Thanks for reading,
The PenTest.WS Development Team