Version 1.8.2 includes several new features and improvements, with maybe the most important being the long awaited IP»Target mod announced last November. Lets step through the major changes in this release…
IP » Target

It is now possible to enter a fully qualified domain name (FQDN) as the Host’s primary identifier. In this example, we’ve shown the possibility for “example.com” and “mail.example.com” as separate hosts. Of course you can still use an IP address to identify a host.
The Import routines have been updated to capture domain names when they have been used to scan a target. For example:
nmap -sC -sV -oA tcp -vv example.com
will now create/update records for the “example.com” host. The Service Command Library automatically uses the Host’s domain name when used as the host identifier:

We’re hoping this change will greatly benefit our pentest community, as well as be a big boost for our bug bounty hunters! Each sub-domain in the program’s scope could have its own Host record, with separate port lists, notes and findings.
Capturing Port State
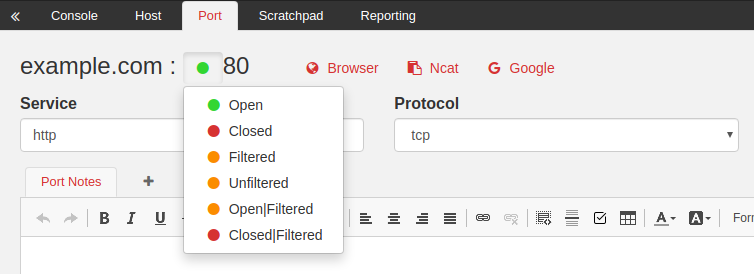
The Import routines have also been updated to capture Port State. This information is included in Nmap’s XML output, and the possible values are Open, Closed, Filtered, Unfiltered, Open|Filtered, or Closed|Filtered.
Port State is displayed in two places. First, on the left side of the screen in the Host List Panel shown in the screenshot at the top of this article. Second, on the Port page, shown in the screenshot above.
As this is a new feature, previously captured ports will need to have their value set manually, or you can re-import the associated Nmap XML file.
Lastly, it should be noted Port State is separate from Port Status, which is a self assigned note to track which ports have been reviewed or may be vulnerable.
Engagement Archives

Got old engagements cluttering up your Mission Control? Click the new Archive button in the top right corner of each Engagement card and it will drop down into the Archived Engagements section. Don’t worry if this section is not visible, it will appear once you archive your first engagement. Click any of the archived engagements to reinstate it to active mode.
And So Much More…
CVE Database –
The Common Vulnerabilities and Exposures (CVE) database is now searchable directly in PTWS (https://pentest.ws/tools/cve). This functions similar to the Exploit-DB feature with full keyword search capabilities.
Engagement Wide Credentials –
On the Engagement Console tab, there is a new Engagement Credentials section which shows credentials from all Hosts within that Engagement.
Export as CSV –
Now you can export Engagements and Hosts as CSV files, in addition to JSON files. Use the Export button in the top right of their respective pages.
Hobby Tier, Yearly Payment Option –
You can now pay a full year of Hobby Tier access through the Membership page. Simply change your plan to yearly, and on your next renewal date you will be changed a single yearly price (currently $39.80)
Be sure to head over to the Feature Request page on the PTWS Support site to submit your ideas for the next version.
Thanks for reading!
PenTest.WS Development Team
