PenTest.WS Pro is just around the corner! Today we’re pushing a small point release to the online version, including both the Free Tier and the Hobby Tier.
Echo Up Goes Base64

One of the first dedicated tools built into PTWS was Echo Up. This tool is used to easily create files through a terminal interface and relies on the echo command. Previously, Echo Up would double encode single quotes and double quotes, and echo the contents line by line into an output file.
Thanks to @4lph4b and the b64chunk.py script, Echo Up is getting new capabilities. More resilient to non-alphanumeric characters, Echo Up now encodes your file into Base64 and uses a series of targeted shell commands to create the file on a remote server.
There are three options: bash, cmd, and Powershell. Each one works slightly differently, but the end result is the same: an exact copy of your file, on the remote server, using nothing but shell commands. You simply copy and paste these commands into your terminal session, no additional ports or protocols needed.
Note: b64chunk.py supports binary files, while the PTWS version currently supports text only.
Venom Builder NOP Sled
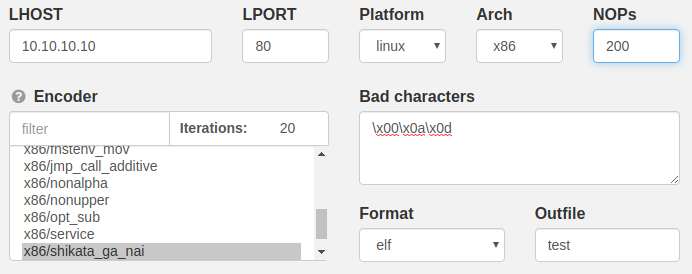
A late addition to this point release, the Venom Builder tool now includes a NOP Sled option.
-n, --nopsled <length> Prepend a nopsled of [length] size
There are a number of options missing from Venom Builder that are available directly through the msfvenom command line. The NOPs option is a great addition and has been requested a few times, and today its here! Keep that feedback coming!
Last, But Not Least – Export Creds

Have you captured usernames, passwords, hashes? Need a quick way to password spray a new service login you just discovered? Want to kick-off a hashcat or john-the-ripper session?
Use the Export Creds button to generate a list of every known username, password, hash in your credentials list and a few different mixtures of each.

Each of the sections in the Export Creds tool is useful in different situations. Sometimes its as simple as reporting your findings – “UN:PW”. Other times it can be a little more complicated.
Here’s a short rundown of each section:
- Usernames: Every known username in your credentials list
- Passwords: Every known password in your credentials list
- UN-PW: A simple combination of username:password
- UN:PW All-U: All permutations of every known username:password, looped around the username
- UN:PW All-P: All permutations of every known username:password, looped around the password. This mode is best for password spraying to reduce the chance of account lockout with large lists.
- Uncracked Hashes: Every known hash in your credentials list that does not also have a password. This is ideal for starting a hashcat or john-the-ripper session.
- UN:Hash All: Every credential record that contains a hash
Note: Export Creds is currently a Host level export and is available on the Host or Port page. Engagement wide credential management is coming in a future release.
PenTest.WS Pro – Status Update
We’re still on track for an end of June release of PenTest.WS Pro. The features are complete and currently being tested. Pricing is nearly settled. Store infrastructure is under heavy development but moving quickly.
We’ll be releasing more information on this blog and Twitter in the weeks ahead. Any unforeseen delays will be announced as soon as possible. Its been a lot of work to get this far, and we’re incredibly excited about the new product.
Thanks for reading, enjoy the new online features, and as always, keep the feedback coming!!
